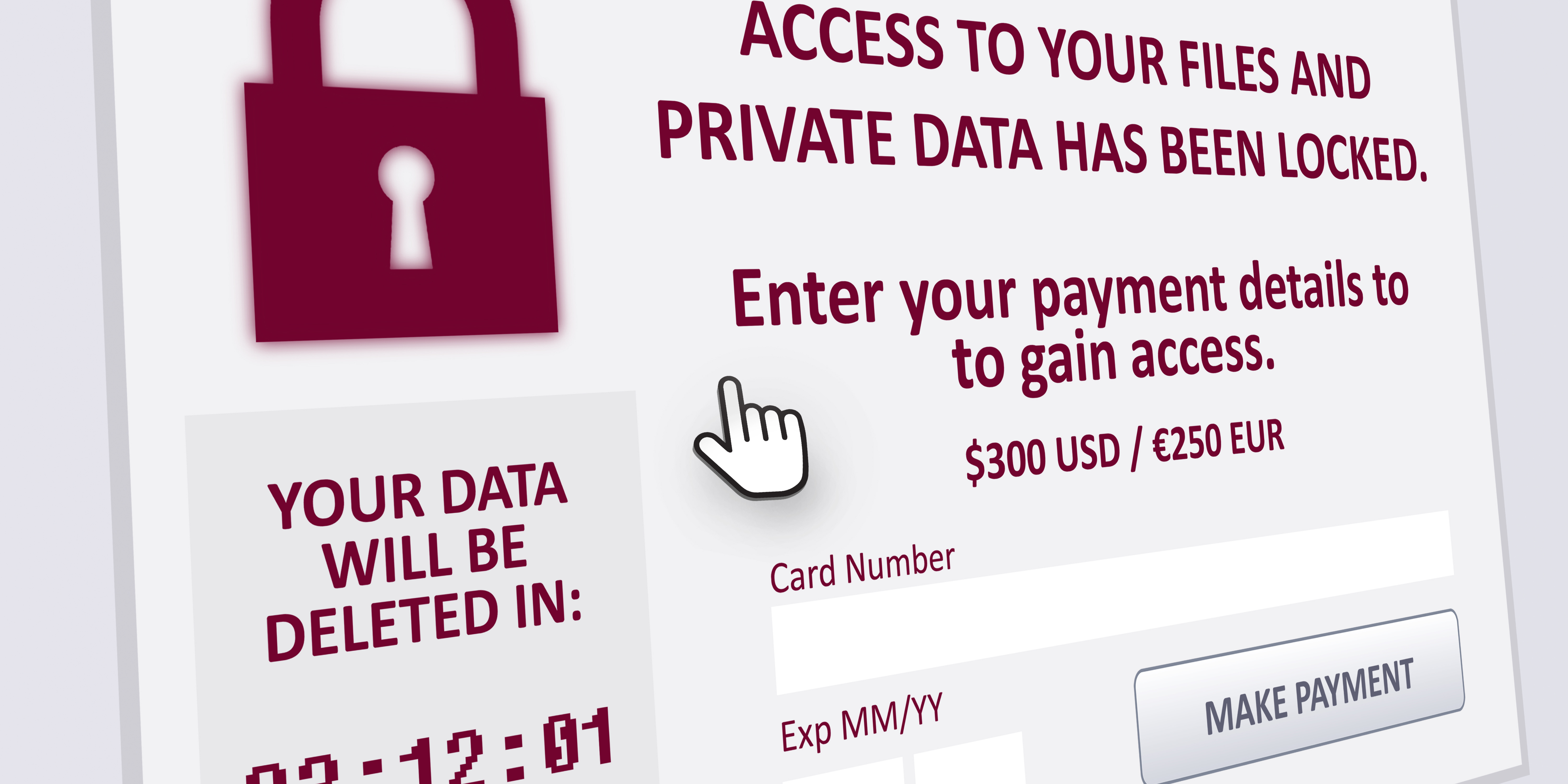
IntroductionIn the ever-evolving landscape of cybersecurity, professionals and enthusiasts alike must stay updated with the latest threats and mitigation strategies. As we navigate through this digital age, three topics have emerged as particularly pressing: Ransomware Attacks, Supply Chain Attacks, and the Zero Trust Architecture. Let’s delve deeper into each of these areas. 1. Ransomware AttacksRising […]
Introduction The digital landscape is ever-evolving, and with it comes both opportunities and challenges. One of the most pressing challenges today is ensuring robust cybersecurity. The SolarWinds hack, a prime example of a supply chain attack, underscores the importance of safeguarding digital assets. Understanding the SolarWinds Security BreachA. Overview of the SolarWinds Hack B. The […]
Introduction With the advent of artificial intelligence (AI) and machine learning in the field of cybersecurity, there has been a significant acceleration in the detection and response capabilities to combat the ever-evolving threats in the digital realm. Understanding AI and Machine Learning Defining artificial intelligence and machine learning Artificial intelligence refers to the simulation of […]
According to most sources, Lorum Ipsum can be traced back to text composed by Cicero in 45 BC. Allegedly Latin scholar established the origin of the text consectetur compiling all the instances of the unusual word ‘consectetur’ he could find and eventually recognized it as a passage from ‘De finibus bonorum et malorum’ (On the […]
Lorem ipsum dolor sit amet, adipiscing elit. Aenean ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, […]