Introduction
In the ever-evolving landscape of cybersecurity, professionals and enthusiasts alike must stay updated with the latest threats and mitigation strategies. As we navigate through this digital age, three topics have emerged as particularly pressing: Ransomware Attacks, Supply Chain Attacks, and the Zero Trust Architecture. Let’s delve deeper into each of these areas.
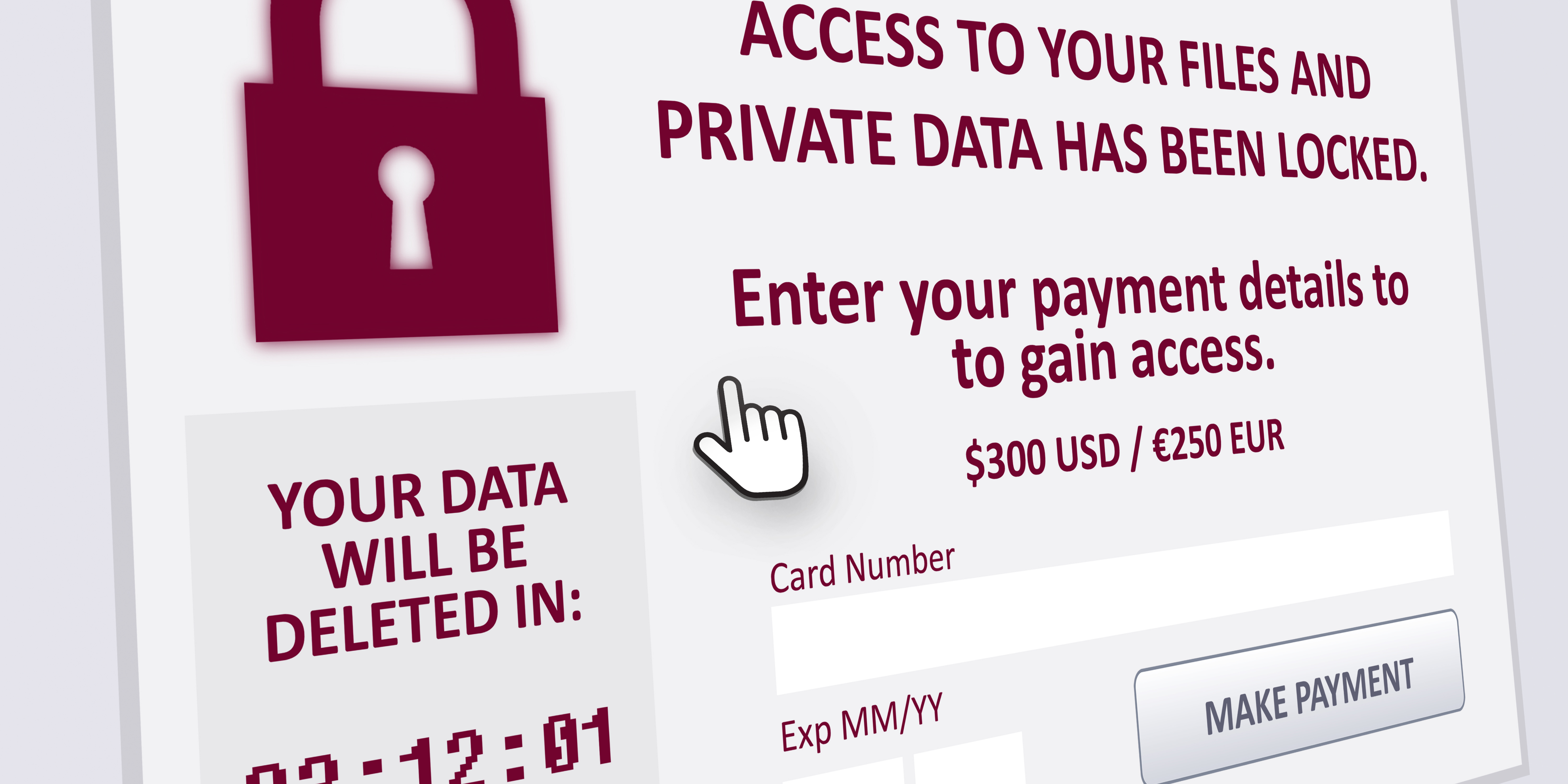
1. Ransomware Attacks
Rising Threat to Global Infrastructure
Ransomware attacks have surged in recent years, targeting critical infrastructure, businesses, and individuals alike. These malicious software attacks encrypt the victim’s data, demanding a ransom in exchange for the decryption key.

Key Points:
- Prevention: Regular backups, updated software, and employee training can significantly reduce the risk of a successful ransomware attack.
- Mitigation: Employing advanced threat intelligence and endpoint security solutions can help detect and mitigate these threats in real-time.
- Response: In the unfortunate event of an attack, having a well-defined incident response plan can minimize downtime and financial loss.
2. Supply Chain Attacks
The Silent Threat
The SolarWinds breach brought to light the vulnerabilities inherent in global supply chains. In a supply chain attack, adversaries target less-secure elements in the supply chain to compromise the primary target.
Key Points:
- Understanding the Risk: Recognize that every vendor and third-party software integrated into your systems can be a potential weak link.
- Regular Audits: Conducting regular security audits of third-party vendors can help in early detection of vulnerabilities.
- Segmentation: Ensure that third-party applications have limited access and are isolated from critical systems.
3. Zero Trust Architecture
Never Trust, Always Verify
With the rise of remote work and cloud computing, the traditional security perimeter has dissolved. Zero Trust Architecture (ZTA) operates on the principle that trust is never assumed, regardless of where the request originates.
Key Points:
- Identity Verification: Every user and device must be authenticated before accessing the network.
- Least Privilege Access: Grant users and devices only the access they absolutely need.
- Continuous Monitoring: Regularly monitor network traffic and user behavior to detect any anomalies.
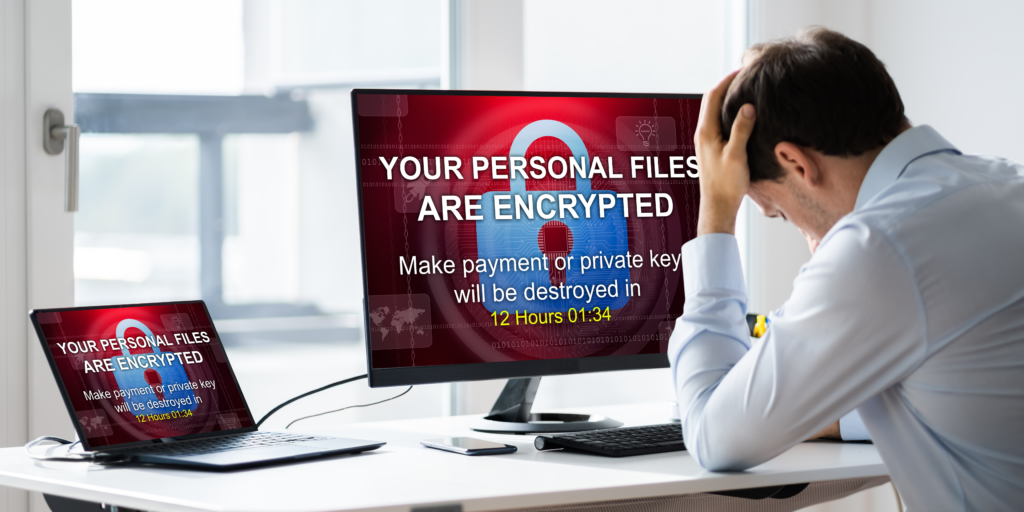
Conclusion
The world of cybersecurity is dynamic, with new threats emerging daily. By understanding and addressing these hot topics, professionals can better safeguard their organizations and personal data. As we move forward, continuous learning and adaptation will be the key to staying ahead of cyber adversaries.
Stay safe and stay informed with Cybxsol.